VMware NSX-T: DFW Rules Not Applying to Virtual Machines vNICs due to Exceeding Maximum Number of Ports
In this blog post, we will address a critical issue encountered during a DFW (Distributed Firewall) rules deployment in VMware NSX-T 3.2.0. We will discuss the problem, its impact, and provide insights into troubleshooting and resolving the issue.
Issue Summary
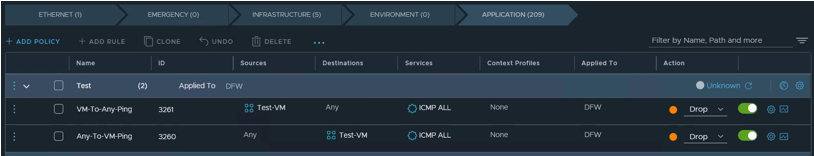
During a recent NSX-T 3.2.0 deployment project, a security policy was created with two DFW rules.
- The first rule aimed to deny ICMP traffic from the virtual machine “TESTVM01” to any destination,
- The second rule aimed to deny ICMP traffic to “TESTVM01” from any source. However,
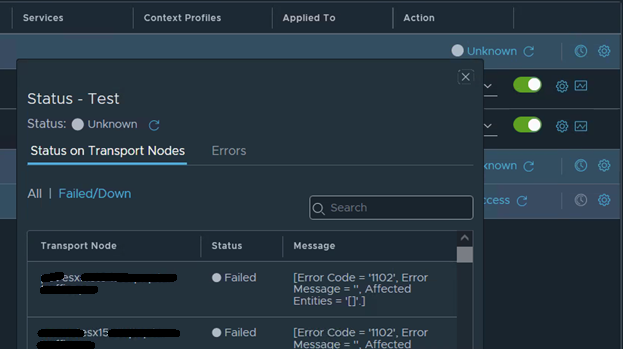
- After publishing the updates, the status of the DFW rules remained “unknown.”
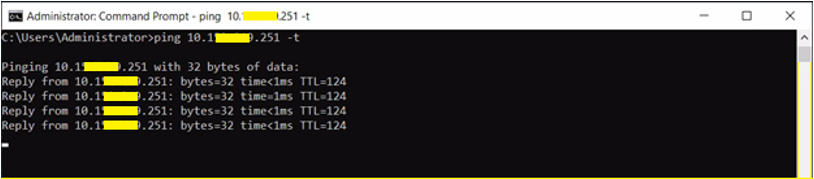
- The issue became evident when pinging to and from “TESTVM01” was successful, indicating that the two DFW rules were not applied to the virtual machine.
- When clicking on the “unknown” status, an error message was received, stating: [Error Code = ‘1102’, Error Message = ”, Affected Entities = ‘[]’.]”

Troubleshotting
To troubleshoot the issue, we performed the following steps:
- Checked the effective enforcement of DFW rules on “TESTVM01” using the below commands on the ESXi host.
# summarize-dvfilter | grep TESTVM01 -A2
# vsipioctl getrules -f nic-128999744-eth0-vmware-sfw.2
- The output revealed that only the DFW rules of the default policy “Default Layer3 Section” were effectively enforced on the virtual machine, and the rules with ID “3260” and “3261” are not applied.

Root Cause
Upon reviewing the configured DFW rules, we identified that the number of ports in a port set exceeded the maximum allowed limit of 15. This discrepancy occurred because the configured range of ports, 50000-59999, counted as 2 ports instead of 1.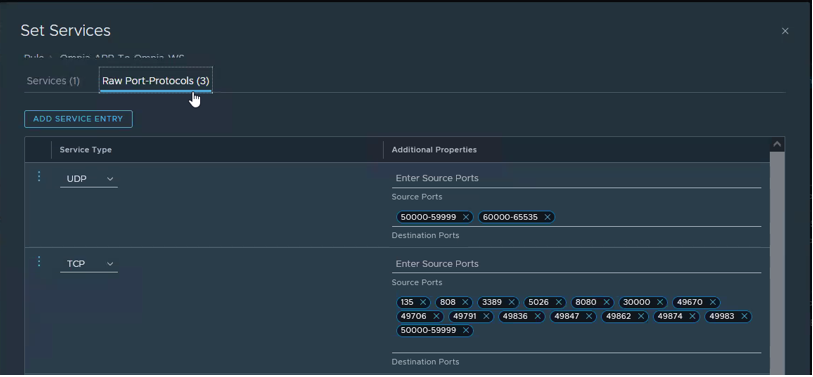
Conclusion
In conclusion, it is crucial to avoid exceeding the maximum number of ports (15) in a port set when configuring DFW rules in NSX-T. Additionally, it’s important to note that a range of ports is counted as two ports rather than one. By adhering to these guidelines, you can ensure the effective application of DFW rules to virtual machine vNICs and maintain a secure network environment.
We hope this blog post helps shed light on the encountered issue and provides valuable insights for successful DFW rules deployment in VMware NSX-T 3.2.0.
Please note that the information provided in this blog post is based on a specific scenario. Thank you for reading, and feel free to leave any comments or questions below.
![]()